- Tech Note: Custom transitions for pushing container view controllers
-
It used to be simple: viruses don’t count as being alive as they just piggy-back on cellular life. This episode of Radio lab provides a fascinating glimpse at newer discoveries which show that it’s not that simple. Some viruses might have evolved—seemingly backwards—from cellular life.
-
Secure your mails
Ever read a post card that wasn’t meant for you?
Without encryption, emails you send and receive are as easy to read as post cards. They could barely have less security, as they are transmitted in plain text. This means that any computer between yours and the recipient’s can study the mails in full without much effort. Encryption prevents your email provider (e.g. Google or Yahoo) from seeing and analysing your email content.
Similarly, even if you receive a mail from steve@apple.com, that doesn’t mean that you got a (delayed) email you can brag about - spoofing senders is easy as there is no process to verify the sender. Signing your emails allows the recipient to gain much more confidence that the email was indeed sent by you - rather than someone else pretending to be you.
This is, unless you sign and encrypt your emails. To me, this is not only a matter of security, but also of executing my right to privacy.
Don’t worry, I’m using HTTPS
Using https is a first step, but not the same. HTTPS makes sure that no one between your client and your email provider can intercept your mails, but it still means that your email provider has access to the content of all your mails.
It also does not help much in terms of securing the long trip from your email provider to your email’s recipient. With email encryption, only you and the recipient1 have access to your email content - your email provider does not have access to it.
Because of that, encrypting emails has one gotcha: you can’t use webmail as it would require your email provider to have your private keys which is a big no-no and besides the point of encrypting your mails in the first place. Make sure you are okay with.
How it works (the technical stuff)
The most common practice for encrypting your emails is using a combination of public and private keys. Basically, you use a signed mail which includes information for the recipient on how to send you encrypted mails - which only you can decrypt (using the private key). It’s like every mail you send comes with a secure return envelope that has a lock which only you can open. If someone sends you a mail, they put the message in the envelope and lock it (i.e., encrypt it using your public key), then send it along the unsafe path of regular email2, and you’ll be able to recreate the original message by decrypting it with your private key.
Check out this nice visualisation using LEGOs (click on it to play the video):
I’m sold. How do I secure my emails?
The mechanism that I’ll walk you through is called S/MIME3 which is similar to securing websites by using HTTPS. Yes, there’s also PGP (and its open-source equivalent GPG) but that is not supported out-of-the-box by most devices and requires additional software4.
Important: If you have more than one email address, you will set up certificates for each of them individually. It should take about 5 minutes to set up the certificates for each email address, depending on the number of your devices. Totally worth it!
Note: The method I’m describing here is for Mac and iOS. It should be similar for other operating systems, but I haven’t tried.
1) Get a certificate
First you need a certificate for your email address: Comodo issues email SSL certificates for free for private use which worked well for me on my iOS 7 devices and Mac OS X 10.9. In Comodo’s Application form, make sure you put in the email address that you would like to have encrypted.
Once you have downloaded your certificate, add it to your Keychain Access. Make sure it shows up in the “My Certificates” category. Mac’s Mail app will now pick it automatically and you’ll get a new set of icons when composing a new message (you might have to restart Mail app).
Signed (no encryption possible)1b) Distribute it across your devices
For iOS devices to the following:
- Open Keychain Access on your Mac, select the certificate (“File” > “Export Items” > “Save”). Make sure file format is set to “Personal Information Exchange (.p12)”, then provide a password.
- Transfer it to your devices, e.g., by emailing it which is fine as long as you picked a strong password.
- Next, install it on your devices by opening that attachment, entering the password and tapping “Install”.
- Finally, add it to your email accounts by opening the Settings app and selecting “Mail, …”” > choose your account > “Account” > “Advanced” > “S/MIME”: enable the section and then enable “Sign” and “Encrypt” by picking the right certificate.
2) Send signed mails
Now you are set to sign emails, which means you can send out your secure return envelopes and you are ready to receive encrypted mails.
3) Sending encrypted messages
To encrypt a message, your recipient needs to do the same thing and they need to send you a message, so that you have their signature (“secure return envelopes”) and can send them encrypted mails.
iOS
At first, emails won’t be encrypted as you need to verify and install the certificate of the person who you want to send an encrypted mail to. If you receive an email from them, watch out for the little checkmark next to their name. Tap their name and install the certificate and your emails to them will then all be encrypted:

Not encrypted. Meh.
A signed and encrypted email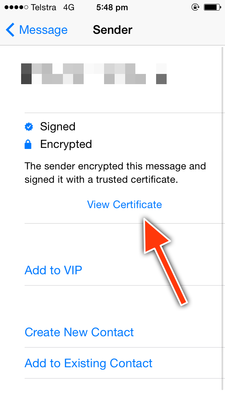
After tapping the sender's name, select 'View Certificate'.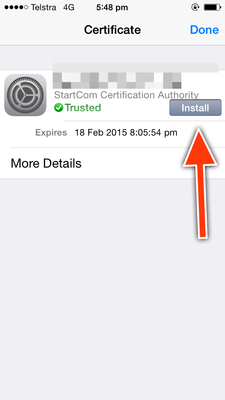
Installing the certificate
Email encrypted! Hooray!Mac
Mail.app on the Mac is installing certificates automatically, as long as they are is from a trusted source. If not, you’ll see a warning on top of the mails and you can manually verify the certificate and set it to “trusted”.
At first I had some issues which were, apparently, caused by my own certificate coming from an untrusted souce (StartSSL, which is quite popular). I couldn’t get Mail.app to encrypt any emails that I tried to sent. I switched to a different certificate authority, Comodo, and then encrypting my emails went smoothly.
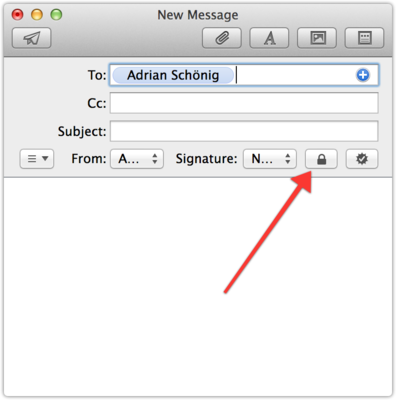
Writing an encrypted and signed email in MailOther operating systems
Android, Linux, Windows, Windows Phone
Limitations
- You now rely on the recipient to do the right thing and to not redistribute the decrypted content. Say, if you receive an encrypted mail, decrypt it and then forward it to someone else without re-encrypting it, the encryption is lost and what was so carefully encrypted before is now out there in plain text again.
- You need to protect your devices which have the private key, so make sure you have a passcode or password or have your fingerprint sensor or retina scanner enabled.
- If you use IMAP, don’t store drafts on the server as those will not be encrypted5.
- Don’t give out your password, make sure it’s one that’s hard to guess, don’t use the same one everywhere, and use 2-factor authorization if possible.
- Of course, watch out for people looking over your shoulder.
- As mentioned above, you won’t be able to use webmail with your encrypted emails.
One last step
In order to make the most out of your encryption, tell your friends, ask them to send you a signed mail, install their certificates, and you can communicate securely and without having to worry about who might be spying on you.
Further reading:
- Secure emails with Apple Mail
- Limitations of secure email
- What Is S/MIME Email and Why Should I Be Using It
-
Well, only your and your recipient’s devices… ↩
-
Still visible to everyone would be whom the mail is addressed to, who sent it, what the subject is and that it’s full of encrypted garbled content. ↩
-
S/MIME stands for Secure/Multipurpose Internet Mail Extensions and, of course, there’s a Wikipedia page for it. ↩
-
I’m using Mac and iOS devices which support S/MIME out of the box while they’d require special plug-ins or apps to work with PGP. ↩
-
Emails that you send and receive that are encrypted will be stored encrypted on your IMAP server - only your client will decrypt them. That means you need to make sure you safeguard and keep your keys, otherwise you won’t be able to read old emails. ↩
-
“The key for Cara is that they’re doing face detection, not recognition,” says Natalie Fronseca, co-founder and executive producer for the Privacy Identity Innovation tech conference, who is very familiar with Cara. “Jason does privacy by design, and that will help him avoid the adverse consequences that often come with data collection.”
It’s only a small step from going from face detection to recognition, and by classifying faces by characteristics (gender, wears glasses, colour, etc.) you can even use detection data to recognise/track individuals.
Inevitably, we will move towards a world where public cameras not only watch us, but software systems actively analyze what we’re doing and what we look like — and actively share this information with businesses and other citizens.
The problem comes when you share this information with businesses and when you don’t have control anymore over who’s tracking you. Since it’s someone else watching you, you don’t have that information by definition.
Compare that to self-trackers such as Fitbits, Google Latitude and similar. You provide the data, rather than someone watching you and inferring things from that.
-
“In the American context, when you use self-quantifying stuff to improve your health you are also sending this information to data aggregators and someone might one day deny you insurance because of it.”
“Even if you are quantifying your own data, if it goes through the cloud service, you may be exploited,” says Lanier. “You are making yourself vulnerable.”
If you join all this DIY Big Data with the other data out there—not only all of our emails and Google searches, but also the sensors in the water system, in medical implants, in stoplight cameras and sound-activated street gunshot detectors—there’s so much of it that one security expert, Bruce Schneier, recently suggested that “the Internet is a surveillance state.”
-
While I occasionally spend a few hours standing on my front stoop scantily clad and in a suggestive pose hoping to gain a little notoriety on Google Maps Street View, I still expect a certain amount of privacy when my family (and several of my neighbors) say it’s time to go back into the house. For some New Yorkers, that expectation of privacy in their own homes went right out (or at least through) the window with the debut of a new photography show at a Chelsea gallery. Photographer Arne Svenson took photos of the residents of the building across the street and created a collection called The Neighbors. According to Salon’s Mary Elizabeth Williams: “None of the photos show the subject’s faces, but the residents of the luxury condo across the street from Svenson are understandably none too thrilled to see their asses turned into artwork – that’s fetching up at up to $7,500 a print, all without their consent.”
- Tech Note: Drawing multi-coloured lines on an MKMapView
- Tech Note: iOS, AddressBook framework and GCD

